The Ultimate vCISO Checklist

What to look for in a vCISO platform
If you’re an MSP/MSSP looking to scale your business and meet growing SME/SMB demand for security services, providing vCISO services can be a profitable option and uplift your business. A vCISO platform will automate vCISO activities like assessing client cybersecurity posture and building and executing strategic remediation plans, without the need to hire an expensive CISO on your team.
Here are some things to keep in mind when looking for a vCISO platform:
Account Management
- Map your current and expected client portfolio. Understanding how many accounts you need to manage will allow choosing a vendor that supports creating and managing separate sub-accounts for each client.
- Plan your team’s headcount for the upcoming years. If you want to grow, you need to delegate ownership to your employees. Find a solution that supports delegating roles and responsibilities to team members.
- Identify the data and information you need for each client. A vCISO platform needs to make security management easier. Look for a solution that offers centralized management and admin-level cross-account visibility for all your accounts and for each sub-account.
Client Onboarding and Cyber Profile Building
- Map the information you need from new clients. An onboarding questionnaire will allow gathering high-level information about new clients, while tailored follow-up questionnaires will allow detailed security posture evaluation. Look for a solution that provides these out-of-the-box.
Security and Vulnerability Scanning
- Scan your client’s externally exposed assets. Discover vulnerabilities and insecure configurations across ports, protocols, encryption, email configuration parameters, technology updates of web applications and more.
- Scan your client’s internal networks. Assess security hygiene and configuration across active directory, endpoints and more.
A solution that performs these scans automatically will provide results in minutes, coupled with remediation options that are connected to a relevant and accurate security plan.
Continuous Security Assessment
- Assess your client’s overall security posture. Many products create a partial picture of security gaps. Choose a solution that parses each client’s cyber profile against industry-specific security standards, regulatory frameworks and industry-specific threat intelligence, and then couples them with the information from the security questionnaires and the scans.
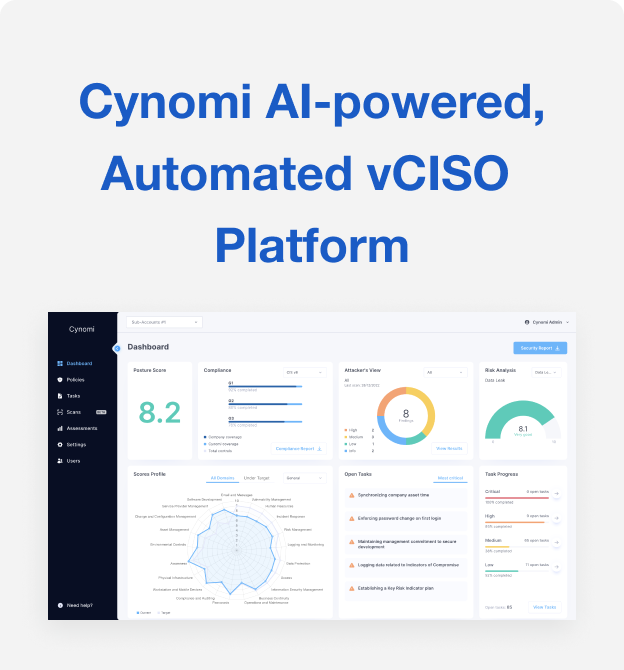
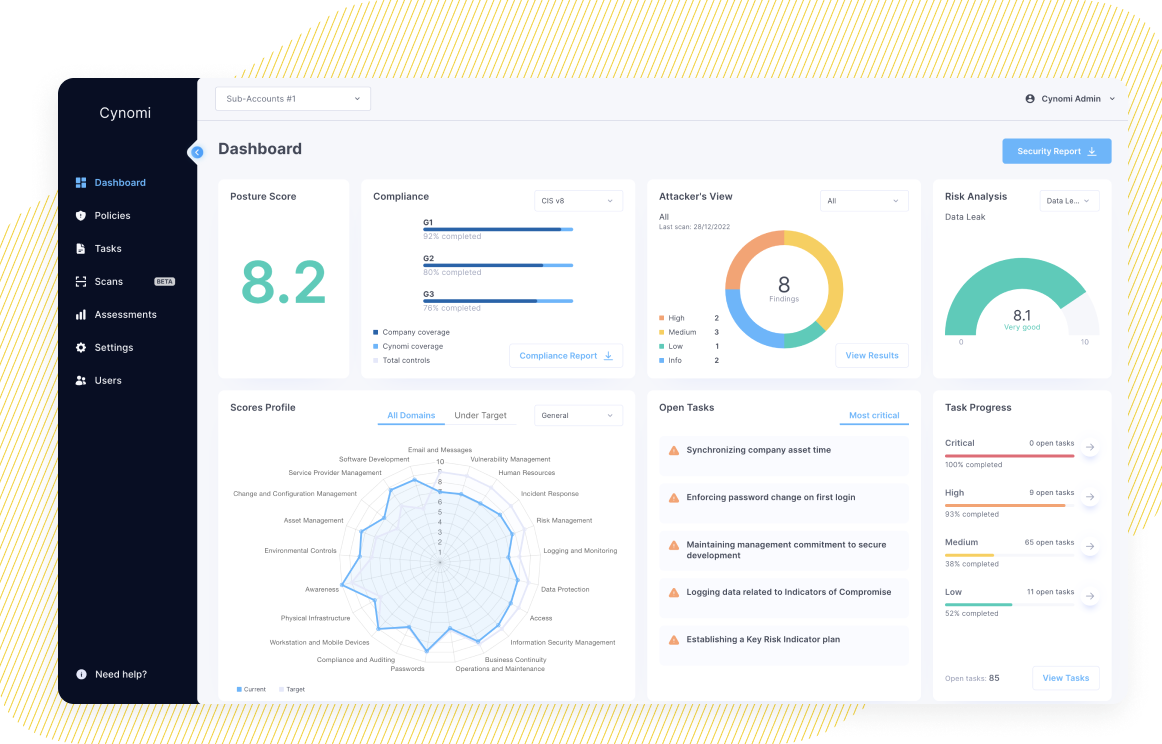
- Calculate your client’s risk score. Understanding where the client stands will help you communicate their security status and generate a remediation plan. A helpful product will provide a dashboard for each client with their overall security posture score and show how it changes over time. It will show each client’s risk score per specific threat type, as well as a remediation plan with tasks that will improve these scores. Since no two clients are identical, the score should be tailored per client according to their industry, risk level and other parameters and should be updated continuously based on the client’s progress.
Compliance Assessment and Reporting
- Assess your client’s compliance posture. A solution that presents the client’s status against CIS v8, ISO 27001, NIST CSF 1.1, NIST CSF2.0, NIST-171, NIST-SSDF, SOC 2, CMMC L1, CMMC L2, GDPR, NIS 2, PCI-DSS, HIPAA security, Cyber Essentials, FTC Safeguard Rule, SEC compliance, ICS Cyber Security, CCPA, FFIEC and others will ensure your clients are ready for any requirement.
- Continuous compliance assessment. Presenting each client’s compliance readiness status against the various frameworks at all times can save your team precious time, help prioritize tasks and allow you to demonstrate progress to end-clients.
- Generate a compliance report for each client. Be sure your vendor includes a customer-facing report with the client’s overall compliance status, maturity level, which controls they have and how they map to which framework and implementation status of improvements.
Security Policy Generation and Management
- Develop security policies for improving your client’s posture. Policies need to be tailor-made and actionable. Find a vendor that creates these automatically while allowing for customization.
- Review policies with the client. Make sure the client can easily follow the requirements and drill-down into each one for details. You can even give them access to the platform.
Task Management and Remediation
- Turn policies and security posture into actionable tasks. Make sure your clients are focusing their efforts on the right things. Leverage global CISO knowledge and AI to turn insights and policies into actionable tasks. Some platforms do this automatically, allowing you to focus on the more challenging parts of the vCISO work.
- Manage and track task execution. Steer away from spreadsheets or email back and forths. Can your product allow for easy management, tracking, assigning and customization of tasks? Make sure it does.
Reporting and Customer Engagement
- Generate comprehensive resorts for your clients and their leadership. Demonstrate progress and allow easy decision-making. Find a solution that automatically produces reports with your client’s posture, risk exposure and compliance readiness status.
- Map the requirements for each report. Make sure the solutions can generate reports with your branding, the current security level, required improvements and compliance gaps.
Continuous Optimization and Value Demonstration
- Continuously update security management. Always be ready and on top of things. Your platform needs to continuously update risk scores, compliance readiness, policies and tasks so you can correctly and expertly guide your clients.
- Demonstrate your value. Take a good look at everything your solution is offering. Make sure it allows you to demonstrate the value of the strategic cybersecurity services you are providing.
The Vendor
- Turn your vendor into a partner. Some vendors are committed to their board or stakeholders. Find a vendor that is committed to you. For example, a vendor whose customers are all partners.
- Evaluate the expertise you need. You can hire expert CISOs for your team or you can choose a platform that’s modeled after the global expertise of multiple CISOs.
- Make time for training. Platform’s need to be intuitive to use. But you also need to make sure the vendor offers training, enablement and support as needed.
To learn more about how Cynomi can help you grow your service provider business and offer vCISO services at scale, let’s talk.

Keeping you safe 24/7
Meet Cynomi Team Learn More