Education

Top IT Security Policies to Implement: Workstation Security Copy
Developing a security strategy and establishing effective security policies constitutes a critical part of the…
Learn More
Top IT Security Policies to Implement: Human Resources
Employees constitute an important organizational cybersecurity protection layer. On the one hand, they can detect…
Learn More
Top IT Security Policies to Implement: Email Security
Email is a critical communication tool for businesses of all sizes, but it is also…
Learn More
5-fold Increase in MSPs and MSSPs Offering vCISO Services, New Report Finds
Cybersecurity attacks are on the rise and the MSP and MSSP market is quick to…
Learn More
How to start a vCISO practice
Introduction MSPs, MSSPs, and cybersecurity consultancy firms are trusted by their clients to deliver best…
Learn More
How Service Providers Can Scale vCISO Services to Boost Revenue and Upselling
Taking your vCISO service to the next level As a service provider – an MSP,…
Learn More
The Risks and Benefits of Starting a vCISO Practice
There has been a marked trend recently of MSPs shifting into the security space, and…
Learn More
Riding the vCISO Wave: How to Provide vCISO Services
Virtual CISO services are in demand like never before. According to Gartner, adoption rates are…
Learn More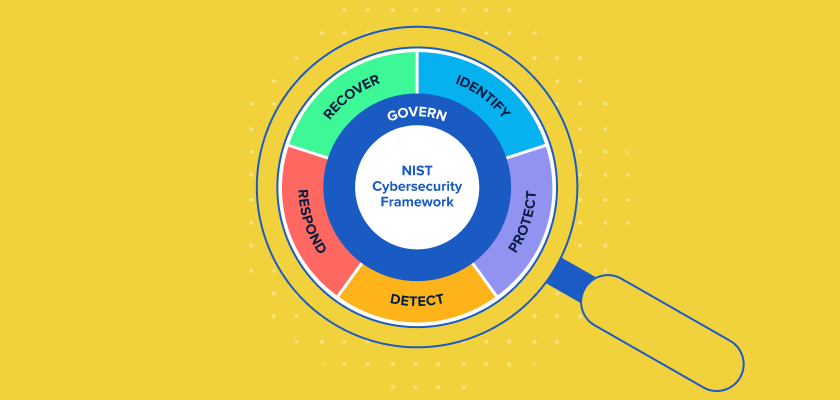
NIST CSF 2.0 and Its Impact on MSPs and MSSPs
On August 8, NIST unveiled the draft for the updated NIST CSF framework. This new…
Learn More
vCISO’s First 100 Days: The Playbook
As a vCISO, you are in charge of developing and implementing the business’s cybersecurity strategy,…
Learn More
The Surge in vCISO Services: Why MSPs and MSSPs Can’t Afford to Lag Behind
The cybersecurity market is experiencing growing demand for robust services and solutions, across all industries…
Learn More
Security Predictions for MSSPs and MSPs 2024
Looking into 2024: Security Predictions for MSSPs and MSPs 2023 is coming to a close,…
Learn More
Managed Service Providers Must Step Up to Help Their Customers Minimize Generative AI Risk
The IT world is becoming increasingly aware of how cybercriminals are harnessing generative AI to…
Learn More
6 Ways to Drive MSP/MSSP Business Revenue with Cynomi
6 Ways to Drive MSP/MSSP Business Revenue with Cynomi MSPs, MSSPs and consultancies can enhance…
Learn More
5 Quick Steps to Create Generative AI Security Standards [+ free policy]
5 Quick Steps to Create Generative AI Security Standards [+ free policy] Organizations are harnessing…
Learn More
How to Choose a vCISO Service Provider: 7 Considerations
In an era where cybersecurity threats have become an unfortunate part of everyday business, organizations…
Learn More
FAQs About vCISO Services
The vCISO concept has been gaining prominence as of late, particularly as small and medium-sized…
Learn More
An easy way for MSPs and MSSPs to boost virtual CISO offering
The Chief Information Security Officer (CISO) position has risen to prominence in recent years due…
Learn More
