Top IT Security Policies to Implement: Workstation Security Copy

Developing a security strategy and establishing effective security policies constitutes a critical part of the CISO or vCISO role. This task is typically time-consuming, especially since each organization requires customized policies that can address its specific structure, security needs, compliance requirements and risk appetite.
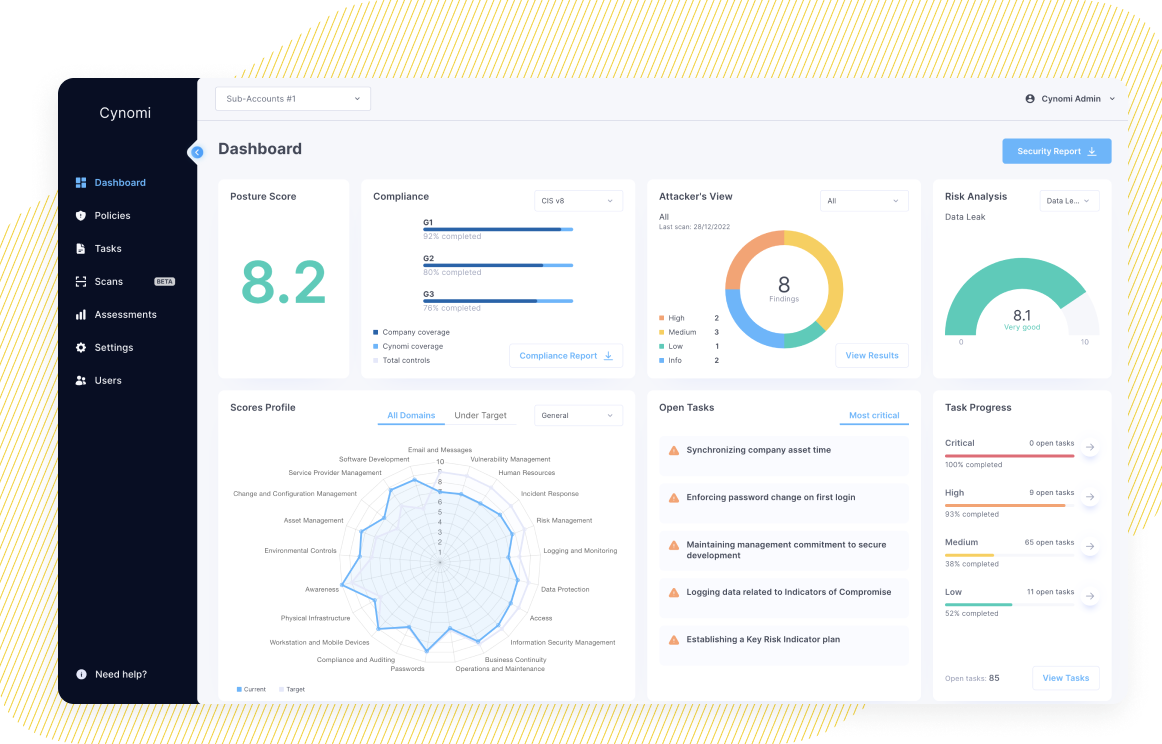
To assist vCISOs in making this task more efficient and effective, we are leveraging the exclusive data and knowledge from Cynomi’s vCISO Platform. Based on this extensive and first-hand information and the derived insights, we’re publishing a complimentary series of blog posts listing the top policies that should be considered by any vCISO and for any organization. Each blog post will also include samples and thoughts for inspiration.
This is our first blog post in this series. It covers Workstation Security, which is one of the most fundamental security policies to be followed.
Why Is This Policy Important?
Workstations, such as computers and laptops, are often a prime target for cyberattacks. These devices, used in all organizations, typically contain sensitive information. They are also often connected to a network, making them vulnerable to a wide range of threats, including malware, viruses, and unauthorized access. Therefore, attackers will frequently target these endpoints while attempting to exploit their weaknesses.
As such, Workstation Security is one of the fundamental and most important policies every organization should follow. A comprehensive Workstation Security policy helps organizations protect data and mitigate cybersecurity risks such as malware and viruses, while reducing the threat of security breaches. Additionally, this policy is required in order to comply with some of the most prominent industry standards and regulations, such as the General Data Protection Regulation (GDPR), the Payment Card Industry Data Security Standard (PCI DSS), and the Health Insurance Portability and Accountability Act (HIPAA).
The Attacks This Policy Help Protect Against
A strong Workstation Security policy helps protect organizations from various malware attacks, including ransomware and Remote Access Trojans (RATs), and from sophisticated phishing attacks that exploit software vulnerabilities and weaknesses in workstations.
Following a workstation security policy also helps protect from Man-in-the-Middle (MITM) attacks, which involve intercepting and altering network traffic between a user’s workstation and a remote server. MITM attacks aim to steal sensitive information or distribute malware across the network.
The Scope of This Policy
The Workstation Security policy applies to all employees, contractors, vendors, and agents that have company-owned (managed) or personal (unmanaged) workstations connected to the organizational network.
Top Controls in This Policy
The controls listed below are the elementary and foundational components of a strong Workstation Security policy. By following them, you can improve the security of your organization’s workstations:
- Strong Password Policy: Implement a strong password policy that requires users to choose complex, unique passwords and to change them regularly. It is also highly recommended to use a password manager.
Why?
Strong passwords are essential for protecting your online accounts from unauthorized access. Weak passwords, such as simple word or number combinations, can be easily deciphered or cracked by hackers using automated tools. In fact, recent research shows that the latest generative AI services can compromise 51% of passwords in under one minute. Strong passwords, on the other hand, are longer, more complex, and include a mix of characters. This makes them much harder to guess or crack. - Multi-Factor Authentication: Use multi-factor authentication (MFA), which requires verification of multiple factors to access a resource. MFA replaces the use of just one factor, such as a password.
Why?
Enabling two-factor or multi-factor authentication adds an extra layer of security to your online accounts. Requiring additional factors, such as a code sent to your phone, in addition to your password, to log in, makes it much harder for hackers to gain unauthorized access to your account, even if they have your password. The chances of attackers being able to provide multiple verification factors is slim, especially if you use factors like biometric verification. - Anti-Malware Protection: Install and regularly update anti-malware and anti-virus software.
Why?
A single malware infection can bring down an entire network, leading to downtime, lost productivity, financial loss, and a damaged reputation. Anti-malware protection can provide real-time protection against malicious software by detecting and removing malware, to help maintain the security of a company’s digital assets. - Operating System and Application Patch Management: Regularly update the operating systems and applications with the latest security patches and updates.
Why?
Patch management helps to keep software and systems up-to-date with the latest security patches and fixes. This helps prevent the exploitation of known vulnerabilities, which can be used by cybercriminals to compromise the organization’s endpoints, network and data. - Firewall Configuration: Configure workstation internal firewalls to restrict incoming and outgoing network traffic.
Why?
Effective workstation firewall configuration provides an additional layer of security against potential network threats. Firewalls can prevent unauthorized access, filter network traffic, detect and block suspicious activity, and stop lateral movement of malware. An internal firewall helps to keep the system and data safe from a wide range of threats, including viruses, malware, and hacker attacks. - File and Folder Encryption: Encrypt workstations’ hard drives. This is especially important for protecting laptops.
Why?
Encryption of files and folders helps protect sensitive data that is stored locally from unauthorized access. Encryption makes it more difficult for cybercriminals to intercept and read confidential information, as the data is scrambled and can only be deciphered with a decryption key. File and folder encryption can also help comply with data protection regulations, and, in some cases, helps protect against ransomware. - User Awareness Training: Educate users on how to recognize and respond to potential security threats and how to follow security best practices.
Why?
In many cases, humans are the cybersecurity weakest link. By raising awareness to cybersecurity best practices and threats, employees can become an effective line of defense against cyber-attacks, thus reducing the risk of security breaches and other cyber threats. User awareness training helps educate employees how to recognize and respond to cyber threats. This includes identifying phishing emails and messages, avoiding social engineering scams, and practicing safe online behavior. - Workstation Administration: Ensure that all operating systems and hardware configurations are centrally managed. Use a minimal amount of local admin accounts and make sure these accounts are securely managed (for example, with Privileged Access Management – PAM solutions).
Why?
Central workstation administration helps ensure that all individual workstations are properly governed, updated and maintained, making them easier to secure. In addition, applying remote administration also allows detecting and remediating security threats quickly, minimizing the impact of security breaches. This reduces the risk of cyber-attacks such as malware infections and data breaches as well as the impact of human error that can occur during manual updates and maintenance. - Locking Workstations: Ensure workstations are locked after a set period of inactivity.
Why?
It is crucial to lock workstations to prevent unauthorized access to sensitive data and systems. When a workstation is left unattended and unlocked, it can be accessed by anyone who has physical access to it, potentially compromising confidential information or allowing for malicious activity. - Backup and Recovery: Regularly backup workstation data and implement recovery procedures.
Why?
Backup and recovery of workstations ensure the availability and integrity of data in the case of a cyber-attack that caused data loss, encryption, or corruption. With a backup, a copy of important data is stored in a safe place, separate from the workstation, and can be used to restore data in the event of an attack. By regularly backing up important data from endpoints and having a recovery plan in place, organizations can prevent data loss and allow business continuity.
Implementing these security controls can help reduce the risk and blast radius of security incidents, and protect sensitive data that is stored on workstations.
3 CISO Takeaways
- Keep Software and Operating Systems Up-to-Date: Cyberattacks often exploit known vulnerabilities and CVEs. By keeping software and operating systems up-to-date, you can significantly reduce the risk of ransomware, malware, phishing and other cyberattacks.
- Implement Multi-Factor Authentication (MFA): Implementing MFA is an effective way to protect workstations from unauthorized access. This is one simple action that significantly reduces the risk of a breach through a workstation.
- Regularly Educate and Train Employees on Cybersecurity: At the end of the day, there are people who use the workstations. As such, regular training and education for employees is key to improving workstation protection. It’s important to conduct regular security awareness training and phishing simulations to enable employees identify security threats in real-time before it is too late.
The controls and practices detailed in this blog post can help you protect your organizational systems and resources. Since cybersecurity is not a “one size fits all” play, we highly recommend consulting with your CISO, virtual CISO, MSSP or cybersecurity consultant before jumping into implementing the suggested controls. To get a full Workstation Security policy tailored to the needs of your specific business, you are welcome to try Cynomi’s vCISO Platform.